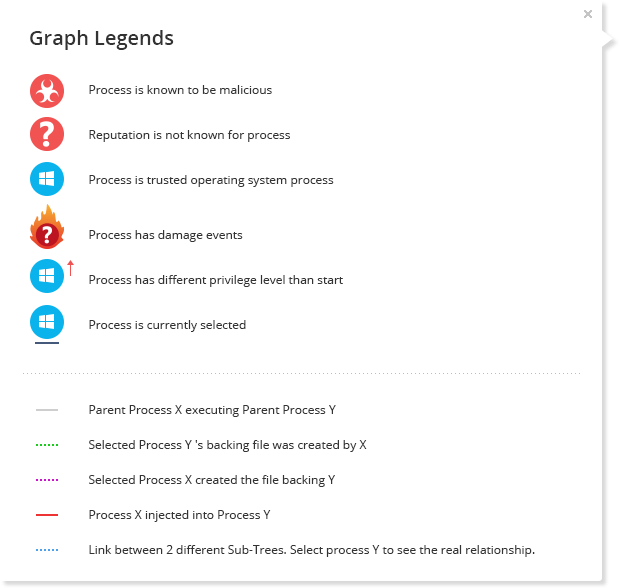
OVERVIEW
REMEDIATION
BUSINESS IMPACT
Process
Security
Reputation
Content
File Ops
Network Ops
Registry Ops
Injection/Hook Ops
Suspicious Events
Damage


| File Name | File Path | File Size (bytes) | Time |
|---|
| Renamed Name | Renamed File Path | Source Name | Source File Path | Time |
|---|
| File Name | File Path | File Size (bytes) | Time |
|---|
| File Name | File Path | File Size (bytes) | Time |
|---|
| File Name | File Path | File Size (bytes) | Time |
|---|
| Rep | Protocol | URL | Action | Dst IP | Dst Port | Src IP | Src Port | Time |
|---|
| Protocol | Expected App Protocol | Dst IP | Dst Port | Src IP | Src Port | Time |
|---|
| Src IP | Src Port | Time |
|---|
| Registry Key | Action | Value | Data Old | Data New | Time |
|---|
| Target | Action | Description | Result | Time |
|---|
| Damage | Resource | Time |
|---|